Cyberprotestos Blog Just another WordPress.com site
OVERVIEW
CYBERPROTESTO.WORDPRESS.COM TRAFFIC
Date Range
Date Range
Date Range
LINKS TO WEBSITE
WHAT DOES CYBERPROTESTO.WORDPRESS.COM LOOK LIKE?
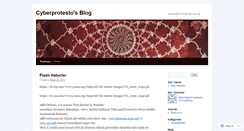
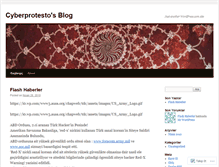
CYBERPROTESTO.WORDPRESS.COM SERVER
BROWSER IMAGE

SERVER SOFTWARE
We discovered that cyberprotesto.wordpress.com is weilding the nginx os.HTML TITLE
Cyberprotestos Blog Just another WordPress.com siteDESCRIPTION
Just another WordPress.com sitePARSED CONTENT
The site had the following in the homepage, "ci aranan Türk Hackerin Pesinde! Amerikan Savunma Bakanliga, red-x nickini kullanan Türk sanal korsanin Siteye Saldiri Asamasinda Bulundu,." I noticed that the web site stated " ABD ordusuna ait yüksek güvenlikli ordu sitesi olan www." They also stated " Microsoftun SQL Servernin frewall kirdi. Yeni bir hackerin daha ABD sorusturma Içinde. 2ci Hackerinda El-Kaide ile Baglantisi varmi diye araştiriliyor."ANALYZE MORE BUSINESSES
Consulting, Training, and Software.
Pusat informasi dunia cyber dan teknologi. Pada malam hari ini saya akan membagikan source code mengenai aplikasi absensi online berbasis android menggunakan JSON. pada sample aplikasi ini media pertukaran datanya menggunakan JSON sebagai media penghubung data mysql ke aplikasi androidnya. Pemilihan kelas dan mata pelajaran. Pada kesempatan kali ini saya ingin membagikan source code secara gratis untuk kamu, berhubung saya lagi baik hati, sekalian bonus buat kamu karena aku udah jarang posting hehehehe .
6 Core Technologies on Jaw Crushers. Frame separation avoids stress concentration and cavity optimization releases greater crushing stroke. Wedge adjustment helps more efficient operation. Better components make the quality more reliable. Elastic limit reduces the shock to machine body. Integrated motor cabinet guarantees more stable power transmission. Six core technologies make C6X Jaw Crusher work more smoothly. Zhoushan 1500-1800TPH Tuff Crushing Line.
Just my thoughts Ladies and Gentlemen, whether right or wrong. Just what I was feeling at the time. Wednesday, September 24, 2008. How 50 Cent Uses Online Video to Build Brand Loyalty. This article was published a while back by Michael Miraflor of how 50 Cent Uses Online Video to Build Brand Loyalty. I thought this article was so GREAT and really broke it down on how 50 cent is capitalizing on this digital world. APPLY! 50 Cent might be the most polarizing figure.
Strona poświęcona przestępczości komputerowej, telekomunikacyjnej i zagrożeniom czającym się w sieci internet. Jak nie dać się oszukać w internecie? Znajdziesz tu kilka podstawowych zasad, które na pewno zminimalizują ryzyko i podniosą Twoje bezpieczeństwo w sieci. Dowiesz się między innymi jak korzystać z e-sklepów, jak dokonywać e-płatności oraz jak korzystać z portali społecznościowch. Jak pozbyć się wirusa UKASH. Zobacz jak szybko możesz to zrobić! Jak usunąć wirus UKASH.